Overview strengthens your cyber security
Cyber attacks and breaches in data security can have serious consequences for organizations in the form of downtime, financial damage and a bad reputation for the company.
The cyber threat against companies rise and the importance of protecting one self against malicious attacks from cyber criminals is getting more important. As head of cyber security it is your responsibility to reduce and minimize this threat against your organization. A proactive approach is consistent scans and surveillance as well as being alarmed when new vulnerabilities arise in applications and infrastructure.
This is where a solution for managing vulnerabilities becomes important in order to quickly get an overview and prioritize necessary steps. BlackstoneOne is a platform that gives you the overview and the options you need, to continuously fix and repair vulnerabilities.
Book a demo
It would be a pleasure to show you why we think our solution is the best.
Book a demo to have the various opportunities and features shown and explained. See how BlackstoneOne can make your vulnerability management much easier.
Please write your email address below – then we will contact you.

With access to the BlackstoneOne portal you will be able to:
- Name targets so you don’t have to crosscheck with documentation of IP lists.
- Group targets so that internal and external users only have access to relevant data.
- Manually initiate scans for validating that vulnerabilities are fixed.
- Receive notifications when there are changes in the vulnerability assessment.
- Hide already assessed vulnerabilities from your dashboard overview.
Why scan with BlackstoneOne?
Our solution is developed with the focus of creating the best options to manage vulnerabilities. Thus we emphasize these two elements.
- The solution automatically scans daily, weekly or monthly. This is a lot more frequent than the traditional ways of vulnerability scanning which takes place 2-4 times a year. With more frequent scanning, the solution is fit to the threat assessment that we see in the moment. Additionally you always have the option to manually initiate a scan whenever you like.
- The solution creates an overview of vulnerabilities that provides you with unique management opportunities. You can name targets, tag targets, limit information regarding vulnerabilities to individual employees and automatically be notified when something happens.
Try it for free
BlackstoneOne develops and maintains
At BlackstoneOne we own, develop and maintain our own vulnerability management platform. This platform makes it possible for us to continuously deliver an updated overview of vulnerabilities in your infrastructure, so that you always know what vulnerabilities you have on the scanned targets.
The technology imports results from multiple scanning technologies to create a comprehensive overview. We take a risk based approach which means that the most vulnerable targets will be analyzed more frequently. Additionally a host discovery will be run on all your IP ranges to ensure that new targets are frequently being registered and included in the continuous scans.
See all releases
Get a free trial
Experience a new way of managing vulnerabilities. Get a comprehensive overview and allow yourself to take a proactive approach. Improve your cyber security today.
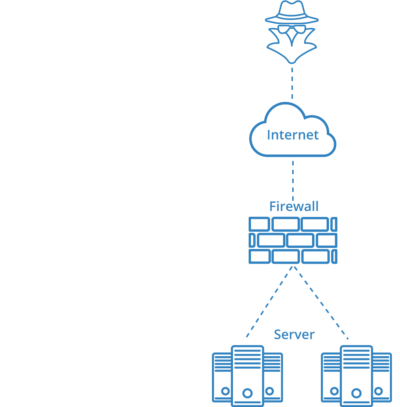
External vulnerability scans
External vulnerability scanning are aimed at the organization’s external/internet-connected infrastructure (for example web servers, mail servers, firewalls etc.)
The scans are conducted as a black-box test which means no further knowledge to the organizations IP addresses (however, whitelisting is recommended to prevent a blockage due to the amount of requests).
An external vulnerability scan discloses known vulnerabilities and flawed configurations regarding external/internet-connected services.
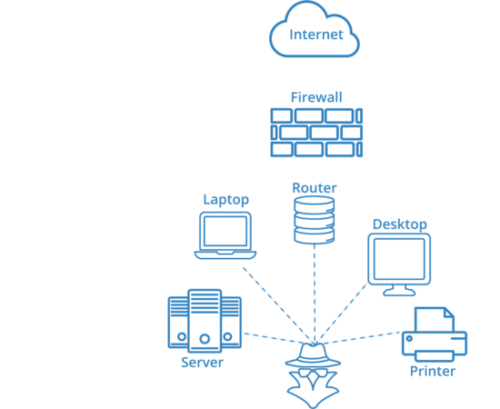
Internal vulnerability scans
Internal vulnerability scanning are aimed at the organizations internal infrastructure (internal servers, switches and routers along with other network equipment).
BlackstoneOne has chosen to use appliances that are to be installed on individual network segments, in order to not scan across your segmented networks for safety reasons.
An internal vulnerability scan discloses known vulnerabilities and flawed configurations regarding services that are exposed on the internal network.
URL/web scans
Aimed towards the company’s websites. The scan runs as a black-box test which means with no further knowledge than the URL. An external vulnerability scan crawls the entire website and discloses, besides regularly known vulnerabilities, information regarding whether the website is vulnerable towards:
- SQL injection.
- Code injection.
- Command injection.
- Path traversal.
- File inclusion.
- XSS – Cross-Site Scripting.
- And many other vulnerabilities.
Features in BlackstoneOne
BlackstoneOne focuses on giving you a present overview, user-friendliness and a user administration that ensures, that the right people receive the information relevant to them.
See all featuresGet a free trial
Experience a new way of managing vulnerabilities. Get a comprehensive overview and allow yourself to take a proactive approach. Improve your cyber security today.



